Digital infrastructure and connected devices are now critical to enterprise operations. From servers and laptops to mobile scanners, these IT assets are everywhere—and so are the expectations for managing them. Visibility, compliance, security, and uptime all depend on knowing where assets are, how they’re used, and when they need attention.
The scale and complexity of today’s environments demand tracking systems that go beyond barcodes and spreadsheets. Across industries, RFID is transforming how digital infrastructure is tracked and managed:
- Logistics companies use RFID to monitor warehouse scanners warehouse scanners and mobile devices across control rooms, sorting centers, and delivery fleets.
- Data centers rely on it for real-time tracking of servers, racks, and networking gear.
- Healthcare providers manage IT and mobile assets across clinical environments.
- University campuses tag devices and media equipment across departments and affiliates.
- High-tech semiconductor manufacturing.
RFID offers a path to automated IT assets tracking at scale. But engineers face real-world challenges—metal surfaces, constrained form factors, mobile use cases, and system integration. Poor tag selection or encoding can create blind spots. Bad placement can lead to unreadable assets and audit failures.
RFID tagging is not just about knowing where devices are — it’s about enabling lifecycle-level visibility: from acquisition and deployment to maintenance and decommissioning. A well-implemented tagging system becomes the foundation for accurate records, cost control, and compliance across the entire digital asset lifecycle.
This white paper, prepared by the Xerafy engineering team, is a field-tested engineering guide to scalable RFID tagging for digital infrastructure. It covers tag design constraints, chip and memory trade-offs, and deployment workflows—drawn from global enterprise rollouts. For engineers building systems that perform under pressure, this is the blueprint.
1. Why RFID for IT Assets Isn’t Plug-and-Play
Tracking IT assets—laptops, tablets, monitors, docking stations, and mobile devices—has long been a challenge for large organizations. These devices are high-value, mobile, and distributed, and manual inventory systems struggle to keep pace. Barcodes require line-of-sight scanning and user compliance. Spreadsheets are error-prone and quickly outdated. Physical audits are disruptive and often incomplete.
RFID offers a path to automation: It enables bulk reading without line-of-sight and without disrupting user workflows. When implemented correctly, it can provide continuous visibility, reduce asset loss, and streamline audits, security, and lifecycle operations.
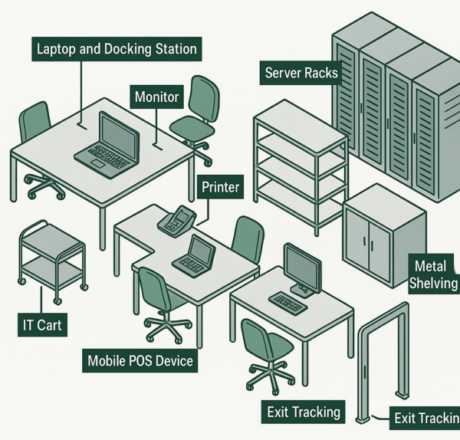
But deploying RFID in IT environments is not as straightforward as tagging pallets or inventory bins. RFID IT asset tracking presents a distinct set of engineering constraints:
- Devices are often housed in metal enclosures or placed on metal shelving, creating RF interference.
- Space is limited, especially on small or irregularly shaped assets such as mobile devices or hand scanners.
- Durability and adhesive reliability are critical due to frequent handling and cleaning cycles over multi-year lifecycles.
- Integration with ITAM, ERP, and ticketing platforms must be seamless for RFID data to add value.
- Deployment scale: Rollouts can involve tens or hundreds of thousands of assets, across hospitals, data centers, warehouses, and campuses.

In each case, RFID tagging had to be engineered for real-world reliability—factoring in surface materials, read environments, form factors, and IT integration.
What works in a lab doesn’t always work in the field. Engineers evaluating RFID for IT assets need more than theory: They need practical, proven guidance on what affects performance, where deployments fail, and how to select components that hold up under operational pressure.
2. RFID Tag Selection for IT Assets: Engineering the Right Fit
RFID tagging in IT environments brings physical and RF constraints that standard tag selection can’t overlook. Engineers must match tag design to real-world conditions—conductive surfaces, tight geometries, mobile usage, and environmental stress.
Metal and Interference Zones
Most IT assets—laptops, docking stations, server racks—contain or are mounted on metal. Even nearby structures like cart frames or shelving can reflect or absorb RF signals, degrading read performance.
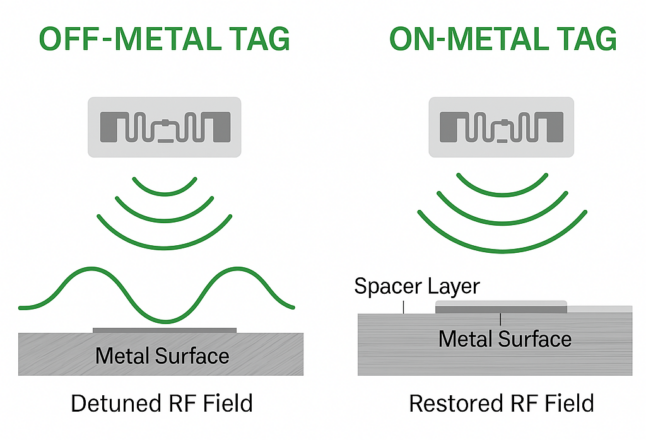
- Use on-metal tags with built-in dielectric spacers to preserve RF tuning.
- Avoid off-metal labels, even in partial-contact scenarios.
A laptop or a rack-mounted switch must use an ultra-thin on-metal label, tuned for close-proximity interference and directional reading.
Space and Geometry Constraints
From barcode scanners to mobile computers, many IT assets lack flat, open spaces for conventional tags.
- Use miniaturized or curved-surface-compatible labels for tight geometries.
- For ultra-compact devices (e.g., USBs, SFPs), embedded tags are often the only viable option.
- Tags must not obstruct ports, vents, or user handling: Engineers should validate that the tag’s physical footprint and mounting method don’t compromise device usability or field performance.
Xerafy’s Metal Skin® series offers ultra-thin on-metal labels optimized for laptops, mobile computers, and other space-constrained IT assets.
0.4mm thin – The Metal Skin® Delta M830 is the thinnest on-metal RFID label and the only one printable using desktop RFID printers, making it ideal for curved or compact IT devices.
The Metal Skin® Titanium M830 is the smallest on-metal RFID label, offering discreet, high-performance tracking optimized for small and high-value electronic devices.
Durability and Handling
IT assets are subject to frequent moves, reassignments, and cleanings. Tag integrity is non-negotiable.
- Choose ruggedized labels or hard tags rated for vibration, abrasion, and environmental exposure.
- Select adhesives based on surface material (e.g., powder-coated metal vs. polycarbonate).
Reject commodity or paper labels. Select tags tested under compression, friction, and temperature cycling.
Mounting and Attachment Methods
Correct tag attachment is just as critical as tag selection.
- Use ultra-thin adhesive labels for flat, static assets.
- For mobile or mission-critical devices, mechanical fastening or embedded installation ensures long-term durability.
- Ensure standardized placement guides or fixtures across asset categories to maintain scan consistency and enable rapid field audits.
In summary, RFID tags are not interchangeable. Performance, reliability, and integration depend on selecting the right tag for the right surface, usage, and deployment context:
- On-metal tuned tags for all conductive surfaces
- Ultra-low-profile formats for space-constrained assets
- Embedded tags for small electronics (e.g., USBs, SFPs)
- Rugged construction and tested adhesives for mobile or high-touch equipment
- Globally tuned RF specs for multi-site deployments
TAG SELECTION FOR IT ASSETS
Asset | Tagging Surface | Recommended | Deployment |
|---|---|---|---|
Laptop | Metal or metalized plastic | Ultra-thin on-metal label (e.g., Metal Skin® Delta) |
|
Desktop / Workstation | Plastic or mixed surfaces | On-metal or hybrid label |
|
Monitor / Display | Coated metal or plastic | On-metal label or hybrid low-profile label |
|
AV Equipment | Plastic or metal | Hybrid or embedded tag (based on shape/usage) |
|
Barcode Scanner | Plastic or partial metal | Ultra-thin or curved-surface on-metal label |
|
Mobile Computer | Plastic or partial metal | Low-profile on-metal or rugged hard tag |
|
Server Chassis | Metal | On-metal label |
|
Network Switch | Metal | Miniature on-metal label |
|
Not all critical devices are on the network. RFID enables traceability for non-IP, non-computing equipment like power supplies, scanners, printers, and test tools that often fall outside the scope of traditional IT discovery systems.
RFID tagged assets can carry metadata linked to depreciation schedules, lease contracts, and end-of-life triggers. This linkage supports more accurate budget planning, timely replacements, and compliant asset disposal
3. Smart Encoding for Scalable Device Traceability
While tag selection determines physical performance, it’s encoding and integration that define whether an RFID tagging project can scale, maintain accuracy, and deliver ROI.
Encoding isn’t just about writing data—it’s about building the logic layer that drives traceability, compliance, and system-wide integrity. A well-defined encoding strategy ensures each tag serves as a trustworthy anchor for asset records, usage history, and operational events.
For engineers, this is where hardware meets data architecture: A flawed EPC structure leads to duplicate assets, failed audits, and orphan tags. A robust one enables scalable deployments with clean data and seamless system integration.
Centralized vs. Field-Based Encoding
Use centralized encoding wherever possible. For field operations, standardize tools and enforce validation at the point of encoding.
Xerafy’s service bureau supports deployment by pre-encoding and customizing RFID tags to match customer-specific data models, saving time and ensuring consistency at scale. This also reduces field complexity and helps enforce standardization across large deployments.
Centralized Encoding (RFID Printers):
- Ideal for new deployments and high-volume tagging
- Ensures EPC structure consistency across all assets
- Allows barcode pairing and pre-labeling
- Requires RFID-compatible on-metal label media
For printer-based encoding, Xerafy provides setup resources and material compatibility guidelines through its Zebra, SATO, and TSC printing guides.
Field Encoding (Handheld or Mobile Devices):
- Used for retroactive tagging or in-place deployments
- Enables real-time asset association
- Prone to manual errors; slower asset throughput
- Requires SOPs and validation tools: Handhelds should confirm EPC structure and perform write-read tests before the tag is applied and locked.

EPC Structure and Serialization
Each RFID tag acts as a persistent digital anchor, enabling the physical device to be tied back to asset records, service logs, and configuration data—even when it’s offline or relocated. This requires careful EPC structuring and consistent encoding across all asset types and sites.
Engineers must define how tags are serialized and how the data aligns with internal systems.
- Use structured EPC formats
- Avoid manual serial number entry—leads to duplicates: Use a generator tool or script for EPCs in centralized encoding
- Finalize and lock EPCs after encoding to ensure data integrity
- Enforce naming conventions across all encoding locations
Tag Memory Use: Keep It Simple
Modern RFID chips like the Impinj M830 support configurable EPC length and optional user memory fields. Engineers need to define how those memory blocks are used.
MEMORY AREA | COMMON USE CASES |
EPC | Electronic Product Code: Unique serialized ID (96 or 128 bits) |
User Memory | Optional, required in some RFID mandates, e.g.: service tag, asset type, or warranty date |
TID | This is the chip ID: Factory-programmed; useful for validation |
Access/Kill Password | Optional; used for security-sensitive assets |
Don’t over-engineer the memory usage and use the EPC for identification. Avoid populating user memory unless your software stack can read and process it. Otherwise, it adds write time and complicates read logic in the field.
When RFID asset tags are mapped to ITAM and ERP systems, they often become inputs for financial workflows — including depreciation schedules, budgeting, and asset retirement planning. Encoding logic must therefore support long-term traceability that ties into finance and audit systems.
RFID Chip Generations and What They Mean for Encoding
Not all RFID chips are created equal. The chip generation inside a tag determines more than just read range—it directly affects encoding speed, EPC structure flexibility, memory availability, and IT system compatibility. Engineers planning large-scale tagging projects must understand these trade-offs to avoid bottlenecks and ensure interoperability across tools, software, and workflows.
GEN2X VS PREVIOUS RFID CHIP GENERATIONS
For IT Asset Tagging Applications
| Feature | Gen2X (e.g., Impinj M830) | Previous Generations (Gen2 / Gen2v2) |
|---|---|---|
| Read Sensitivity | Very high – optimized for dense, reflective environments | Standard to improved |
| Tag Size | Supports ultra-small and ultra-thin on-metal labels | Medium to small formats |
| Encoding Speed | High-speed with FastID (up to 20% faster inventory) | Baseline to moderately improved |
| Memory & Access | Fast, flexible memory access with block-level control | Limited or slower user memory access |
| Security & Privacy | Protected Mode, authentication, and EPC privacy features | Basic access/kill passwords, optional permalock |
| Serialization | FastID for efficient EPC-to-TID linking and serialization | Manual or basic EPC serialization |
| Power Efficiency | Ultra-low power for longer range and dense reads | Moderate to improved |
| Read Range Efficiency | Reliable reads even with compact or embedded tags | Tuning-dependent; range drops on smaller tags |
| IT System Integration | Designed for scalable ITAM, audit readiness, ServiceNow, JAMF | Legacy-compatible, limited enterprise integration |
Integration with ITAM, ERP, and Support
Encoding must align with the asset’s digital twin.
- ITAM platforms (e.g., ServiceNow, Lansweeper) must recognize the EPC
- ERP (e.g., SAP, Oracle) systems need lifecycle visibility
- Ticketing systems (e.g., Jira, Remedy) must link to serialized tags for support and audit trails
Common points of failure include mismatched asset IDs between EPCs and system records, inconsistent field mapping, and lack of real-time synchronization. These create blind spots, duplicate entries, or failed asset associations, that undermine the system.
- Include data model alignment as a key responsibility for engineering + IT teams.
- Consider emphasizing validation loops post-encoding to verify asset-tag linkage before deployment.
Audits and compliance reviews increasingly rely on RFID systems to verify asset existence, location, and status. A robust RFID deployment creates a verifiable audit trail with each scan — reducing the risk of data mismatches, unauthorized asset movement, or incomplete records during regulatory reviews.
RFID tagging typically complements either agent-based or agentless IT asset discovery methods. Agent-based approaches install software to report usage and location, while agentless methods rely on network discovery tools. RFID adds a physical layer of verification, especially valuable for mobile, disconnected, or non-networked devices.
RFID-based asset visibility supports ITIL-aligned practices for change, incident, and configuration management. Accurate tag-to-system linkage enables faster root cause analysis, audit-ready logs, and efficient response workflows.
Encoding Checklist: Getting RFID Right the First Time
<> EPC structure aligns with asset taxonomy and site structure
<> Encoding method validated (printer or handheld)
<> User memory fields used only if supported
<> Tags linked to asset in ITAM/ERP before deployment
4. From Lab to Rollout: Engineering RFID Deployments That Work
Successful RFID systems aren’t just engineered — they’re deployed. Lab tests and spreadsheets don’t reflect the physical realities of IT environments: inconsistent surfaces, fluctuating RF conditions, or multi-site complexity. This section captures the operational know-how engineers need to move from pilot to production at scale.
Field Validation: From Spec Sheets to Real-World Results
A tag that works in theory can still fail in practice. Engineers must validate in the actual deployment environment:
- Surface compatibility: Test adhesion, detuning, and mounting on real asset materials.
- Read reliability: Measure performance from expected scanner positions (e.g., walk-by handhelds, fixed exit readers).
- Environmental noise: Identify RF disruptions from metal racks, cables, HVAC, power supplies, carts.
- Software flow: Ensure EPCs are correctly encoded, read, and pushed to ITAM/CMDB without data loss or delay.
Best practice: Use a small, representative asset pool (~20 items) to run end-to-end validation in the real-world workflow before scaling.
For high-value or portable assets, RFID supports anti-theft strategies through fixed reader zones, exit tracking, and tamper-evident tag designs. Integration with security systems can trigger alerts if tagged assets move outside defined zones.

Tag Application: Surface Prep and Placement Discipline
Even the best tag will fail if poorly applied. Engineers must define RFID tagging standards.
Checklist for reliable tag application:
<> Clean surface (isopropyl alcohol recommended)
<> Firm, even pressure during placement
<> Curing time for adhesive, especially in humid/cold zones
<> Avoid vents, seams, and moving parts
<> Use photo guides or templates for consistency
For high-value or high-risk assets, consider tamper-evident labels or mechanical fastening.
In enterprise environments, tags are also used to link physical assets to maintenance records, warranty tracking, and repair logs. Ensuring consistent EPC formatting and encoding enables integration with support systems for preventive maintenance and operational uptime.
Infrastructure Planning: Readers, Antennas, and Scanning Workflows
RFID tag performance is shaped by the full deployment environment—not just the tag. For example, a fixed reader near an IT storeroom exit may require directional antennas and tuned read zones to avoid false reads from adjacent shelves.
Engineers should validate and optimize the following elements:
- Scanning mode: Choose between walk-by handhelds, fixed checkpoints, or hybrid scanning setups.
- Reader setup: Configure reader power levels, antenna gain, and coverage zones to ensure consistent reads.
- Tag-reader pairing: Match tag specs with frequency region (FCC/ETSI), polarization, and tag geometry.
- Environmental RF dynamics: Identify and mitigate interference caused by metal racks, HVAC, power supplies, and reflective surfaces.
Multi-Site Deployment: Standardization With Local Flexibility
Scaling to multiple facilities introduces real-world variation in infrastructure, asset mix, and regulations. Engineers must balance global standards with local realities:
- Define a controlled set of approved tag types by asset class
- Pre-test regional performance (e.g., FCC in the U.S., ETSI in Europe)
- Enforce common encoding formats and naming conventions
- Centralize asset registry tracking, even with decentralized tagging
- Validate that local workflows and infrastructure match head-office assumptions
- Prepare location-ready kits including pre-encoded labels, mounting templates, SOPs, and validation tools
Certain environments — such as university labs, healthcare systems, or logistics hubs — require tracking of mobile or shared devices. RFID-tagged assets can be integrated with check-in/check-out workflows to maintain chain-of-custody records, reduce loss, and support internal accountability.
In environments such as data centers, engineers must factor in equipment density, airflow requirements, and RF interference, with data centers re-architected with RFID to meet these constraints.

5. From Tag to System — Engineering RFID That Performs
RFID tagging for IT assets and devices isn’t just a sourcing decision — it’s a system design challenge. Field-proven deployments show that success depends on engineering discipline: matching the tag to the environment, validating performance under operational conditions, and aligning data capture with enterprise systems.
The takeaway: Not all tags are created equal. Tagging that works at scale requires fit-for-purpose design — tuned for surface, form factor, and RF behavior — backed by reliable encoding and integration.
Before scaling, engineers must confirm:
- Tags perform consistently across device types and locations
- Application methods are standardized and repeatable
- Encoding logic maps cleanly to ITAM, ERP, and support systems
When the details are right, RFID transforms from a tracking tool into a foundational layer of operational intelligence.
Need help validating your RFID tagging system? Consult with the Xerafy engineering team to review tag selection, encoding logic, and system integration—before you scale.
Xerafy is a pioneer in Industrial RFID, bringing to market several innovations that enable advanced identification and automation capabilities in manufacturing.
In addition to a complete range of field-proven RFID tags available off-the-shelf, Xerafy offers Custom RFID Tags services, covering everything from a personalization service bureau to custom-design engineering capabilities.













